How does the screen "ghost" come about? How to remove?
"Ghosting" is commonly used to describe the residual image pattern on recycled screens. After recovery, many tiny hardened ink dots and emulsion particles adhere to the wire wall, affecting the ability of the next mesh ink to pass normally. In a bad situation, when the screen plate is reapplied and exposed to generate a new image, the hardened particles in the residual image portion will absorb the ink and thus appear a blurred pattern on the print.
Such ink/emulsion particles can generally be eliminated with strong cleaning chemicals such as defogging agents. The defogging agent decomposes the residual emulsion on the wire mesh wall and returns the mesh to a naturally stretched state.
There is another form of "ghosting" in which, when a new emulsion has been coated and subjected to a specific exposure, the fuzzy inconsistency pattern will also be partially contiguous when printing with this new screen image. Districts are presented. The cause of this problem can be traced back to the positive film itself.
There is a discontinuity in the continuous area of ​​the image, in other words, the image area should have enough opacity to block the passage of exposure light, but some areas will not reach the ideal density so that the light reaches the underlying emulsion layer. And a certain amount of actual exposure is generated. After development, the part of the mesh that should completely dissolve ink will be blocked and an unnecessary printing pattern will be produced on the printed product. The solution to this problem is to make full use of the density meter's function to use it to detect the highest density (Dmax) of the continuous tone zone of the positive film and the lowest density (Dmin) of the non-density transmission zone.
The third potential reason is the old and worn screen fabrics. In the long-term rolling, expansion and cleaning recovery process, the screen silk fabric will become more damaged flat plate, so that in the printing, this locally deformed thread brings changes in the ink transfer characteristics, compared with the intact part These areas will form additional pattern features on the prints. When this physical damage occurs, the only thing that can be done is to replace the screen screen.
6.4 Disc Copy Protection Technology
Common optical disk copy protection technology:
1. Cactus Data Shield:
A protection technology for music CDs, divided into CDS-100, CDS-200, CDS-300 three versions. This type of optical disc incorporates an automatic recording sector, which causes interference during the reproduction of the CD-ROM and makes it unreadable. However, less compatibility is used.
2, CD-Cops:
For data software discs, add a shell to the installer. When installing, ask for a verification password. There will be a CDCOPS.DLL file for this technique on the CD. It is an older optical disc encryption technology.
3, SecuROM (New):
For software disc protection, add SecuROM ciphertext during the disc compression process, and read the SecuROM ciphertext during the software operation to verify. There are CMS16.DLL, CMS_95.DLL, CMS_NT.DLL and other feature files on the CD. Used more widely.
4, DiscGuard (CD Guardian):
For software discs, the main application file is encrypted. Add digital signatures to the platen and generate the installation serial number, and compare the consistency when executing the file. There are IOSlink.VXD, IOSlink.SYS files on the CD.
5, TAGES:
One of the newer data disc protection technologies, the specific encryption method is unclear. Less used.
6, Star Force:
It is also one of the newer software disc protection technologies. The protection mechanism is similar to CD-Cops but it has been improved. Many game softwares currently use this technology.
7, Dummy files (virtual files):
For data discs. This is known as an oversized file, which is created by modifying the file allocation table of the disc to create an oversized fake file. Make the usual CD-R unable to accommodate. The disc capacity is generally greater than 700 to 2000M.
8, SafeDisc (security disk):
Data CD protection technology has been available in 1.0, 2.1, 2.2, 2.3, 2.4, 2.5 and so on. Earlier versions added digital signatures (subcodes) on the base of 2352 in the process of disc suppression. Newer The version also adds the Weak Sector. There are 00000000.016, 00000000.256, 00000001.tmp and other characteristic files on the disc.
We offer a wide range of plastic accessories with beautiful appearance and high quality.
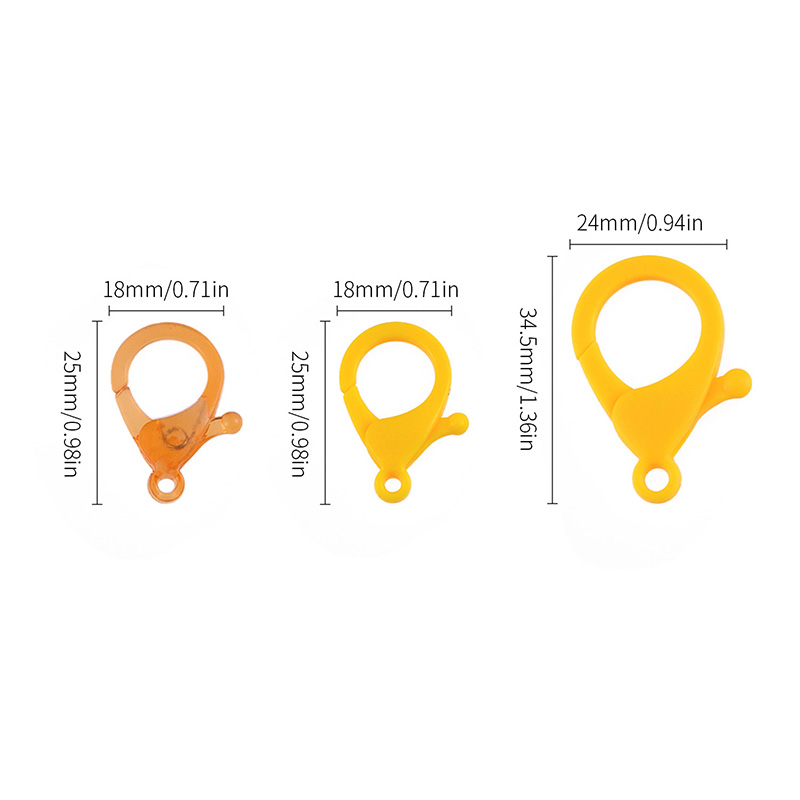
Because the shape of the Plastic Lobster Clasp Hook resembles a lobster, so it is also called Plastic Lobster Claw Clasp.We have different colors of Plastic Lobster Clasps to choose from, the transparency is also different, if you have the color you want, you can contact us to customize.

We have different sizes of Plastic Lobster Clasps, and we can also customize the size you need.
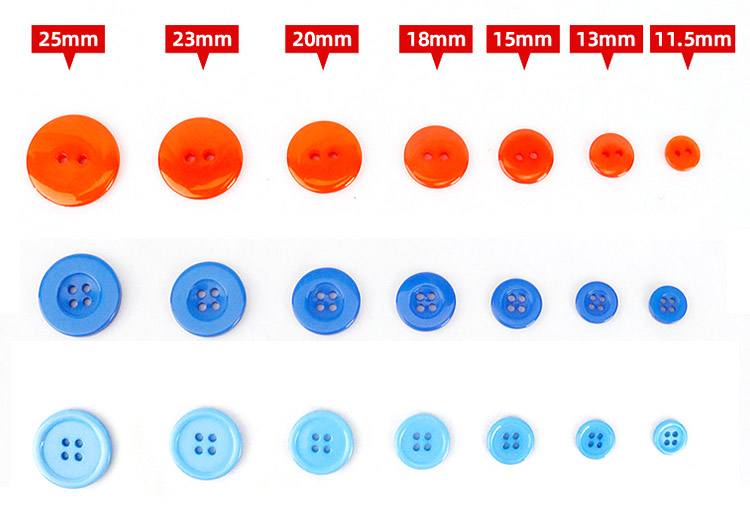
2.Plastic Button

3.Plastic Chain

Our plastic chains have a wide variety of styles, not only in different colors and sizes, but also special chains, and the length can also be customized, welcome to inquire.
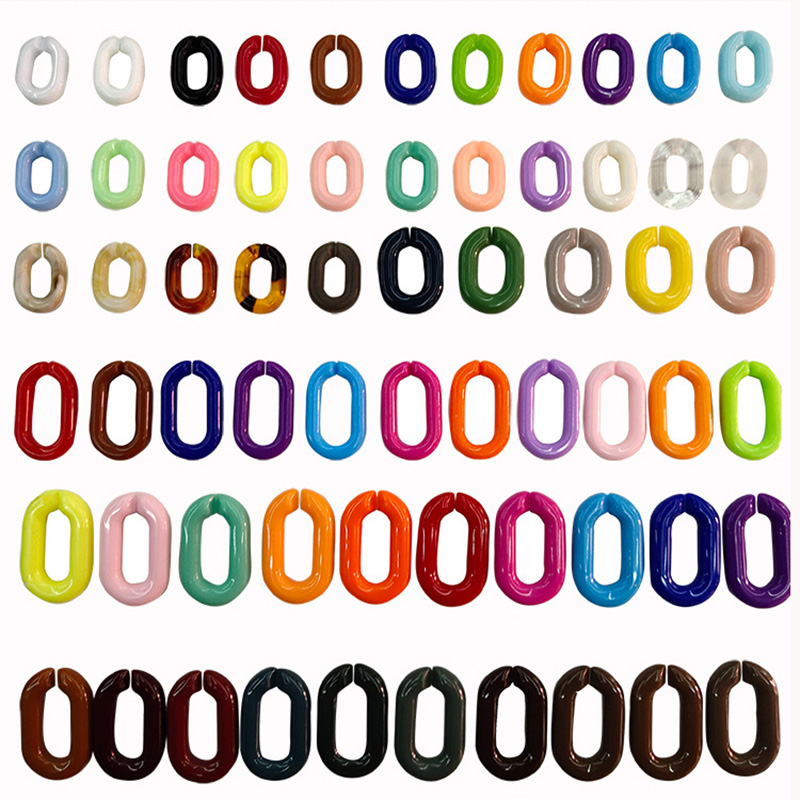
There are many other styles of plastic accessories, come to consult us for more new information about plastic accessories.
Plastic Snap Hook,Button Plastic,Plastic Chain,Plastic Lanyard Hooks,Plastic Lanyard Hook
Shenzhen Yiyixing Zipper Manufacture Co.,Ltd , https://www.nicekeychain.com